GATE CSE
P: Always finds a negative weighted cycle, if one exist s.
Q: Finds whether any negative weighted cycle is reachable from the source.
$$T(n) = \begin{cases} n & n \leq 3 \\ T(\frac{n}{3})+cn & \text{ otherwise } \end{cases}$$
Which one of the following represents the time complexity of the algorithm?
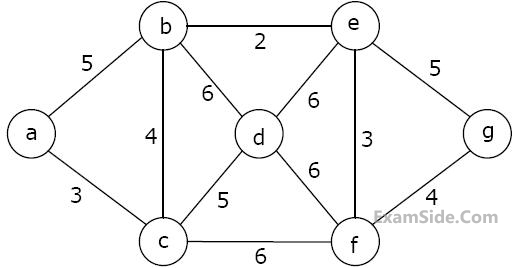 Which one of the following is NOT the sequence of edges added to the minimum spanning tree using Kruskal’s algorithm?
Which one of the following is NOT the sequence of edges added to the minimum spanning tree using Kruskal’s algorithm?We wish to find the length of the longest common sub-sequence (LCS) of X[m] and Y[n] as l(m,n), where an incomplete recursive definition for the function I(i,j) to compute the length of the LCS of X[m] and Y[n] is given below:
l(i,j) = 0, if either i = 0 or j = 0
= expr1, if i,j > 0 and X[i-1] = Y[j-1]
= expr2, if i,j > 0 and X[i-1] ≠ Y[j-1]Which one of the following statements would be TRUE regarding the dynamic programming solution for the recursive definition of l(i, j)?
We wish to find the length of the longest common sub-sequence (LCS) of X[m] and Y[n] as l(m,n), where an incomplete recursive definition for the function I(i,j) to compute the length of the LCS of X[m] and Y[n] is given below:
l(i,j) = 0, if either i = 0 or j = 0
= expr1, if i,j > 0 and X[i-1] = Y[j-1]
= expr2, if i,j > 0 and X[i-1] ≠ Y[j-1]Group 1
P. Regular expressionQ. Pushdown automata
R. Dataflow analysis
S. Register allocation
Group 2
1. Syntax analysis2. Code generation
3. Lexical analysis
4. Code optimization
Which one of the choices given below is closest to the minimum permissible rate at which sequence numbers used for packets of a connection can increase?
I. M'= Me mod n
M = (M')d mod n
II. ed ≡ 1 mod n
III. ed ≡ 1 mod $$\phi $$(n)
IV. M'= Me mod $$\phi $$(n)
M = (M')d mod $$\phi $$(n)
Suppose that the sliding window protocol is used with the sender window size of 2l, where l is the number of bits identified in the earlier part and acknowledgements are always piggy backed. After sending 2l frames, what is the minimum time the sender will have to wait before starting transmission of the next frame? (Identify the closest choice ignoring the frame processing time.)
What is the minimum number of bits (I) that will be required to represent the sequence numbers distinctly? Assume that no time gap needs to be given between transmission of two frames.
0, 255, 1, 4, 3, 8, 133, 159, 216, 129, 63, 8, 48, 32, 73, 92, 155.
Which one of the following memory block will NOT be in cache if $$LRU$$ replacement policy is used?

What is the number of cycles needed to execute the following loop?
For $$\left( {i = 1} \right.$$ to $$\left. 2 \right)$$ $$\left\{ {{\rm I}1;{\rm I}2;{\rm I}3;{\rm I}4;} \right\}$$
Suppliers(sid : integer, sname : string, city : string, street : string)
Parts(pid : integer, pname : string, color : string)
Catalog(sid : integer, pid : integer, cost : real)
Consider the following relational query on the above database:SELECT S.sname
FROM Suppliers S
WHERE S.sid NOT IN
(SELECT C.sid
FROM Catalog C
WHERE C.pid NOT IN
(SELECT P.pid
FROM Parts P
WHERE P.color<> 'blue'))Suppliers(sid : integer, sname : string, city : string, street : string)
Parts(pid : integer, pname : string, color : string)
Catalog(sid : integer, pid : integer, cost : real)
Assume that, in the suppliers relation above, each supplier and each street within a city has a unique name, and (sname, city) forms a candidate key. No other functional dependencies are implied other than those implied by primary and candidate keys. Which one of the following is TRUE about the above schema?T1: R1[ x ] W1[ x ] W1[ y ]
T2: R2[ x ] R2[ y ] W2[ y ]
S1: R1[ x ] R2[ x ] R2[ y ] W1[ x ] W1[ y ] W2[ y ]
S2: R1[ x ] R2[ x ] R2[ y ] W1[ x ] W2[ y ] W1[ y ]
S3: R1[ x ] W1[ x ] R2[ x ] W1[ y ] R2[ y ] W2[ y ]
S4: R2[ x ] R2[ y ] R1[ x ] W1[ x ] W1[ y ] W2[ y ]
I. $$\pi_{R-S}(r) - \pi_{R-S} \left (\pi_{R-S} (r) \times s - \pi_{R-S,S}(r)\right )$$
II. $$\left\{t \mid t \in \pi_{R-S} (r) \wedge \forall u \in s \left(\exists v \in r \left(u = v[S] \wedge t = v\left[R-S\right]\right )\right )\right\}$$
III.$$\left\{t \mid t \in \pi_{R-S} (r) \wedge \forall v \in r \left(\exists u \in s \left(u = v[S] \wedge t = v\left[R-S\right]\right )\right ) \right\}$$
IV. Select R.a, R.b
From R, S
Where R.c = S.c10, 3, 6, 8, 4, 2, 1
The maximum number of times leaf nodes would get split up as a result of these insertions is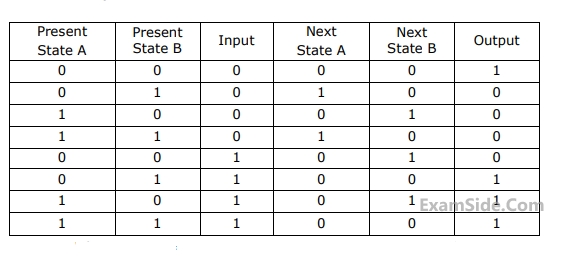
If the initial state is $$A = 0, B=0.$$ What is the minimum length of an input string which will take the machine to the state $$A=0, B=1$$ with Output$$=1?$$
"$$Gold\,and\,silver\,ornaments\,are\,precious$$"
The following notations are used:
$$G\left( x \right):\,\,x$$ is a gold ornament.
$$S\left( x \right):\,\,x$$ is a silver ornament.
$$P\left( x \right):\,\,x$$ is precious.
$${\rm I}.$$ $$\,\,\neg \forall x\left( {P\left( x \right)} \right)$$
$${\rm I}{\rm I}.\,\,\,\,\,\,\neg \exists x\left( {P\left( x \right)} \right)$$
$${\rm I}{\rm I}{\rm I}.\,\,\,\,\,\,\neg \exists x\left( {\neg P\left( x \right)} \right)$$
$${\rm I}V.\,\,\,\,\,\,\exists x\left( {\neg P\left( x \right)} \right)$$
Which of the above are equivalent?

Which one of the following is equivalence to $$P \vee Q$$?

Which one of the following choices is correct?
If the probability that the face is even given that it is greater than 3 is 0.75, which one of the following options is closest to the probability that the face value exceeds 3?
On a demand paged virtual memory system running on a computer system that has main memory size of $$3$$ page frames which are initially empty. Let $$LRU,$$ $$FIFO$$ and $$OPTIMAL$$ denote the number of page faults under the corresponding page replacement policy. Then
$$4, 34, 10, 7, 19, 73, 2, 15, 6, 20$$
Assuming that the head is currently at cylinder $$50,$$ what is the time taken to satisfy all requests if it takes $$1$$ $$ms$$ to move from one cylinder to adjacent one and shortest seek time first policy is used?
 Which one of the following statements is TRUE if all three processes run concurrently starting at time t = 0?
Which one of the following statements is TRUE if all three processes run concurrently starting at time t = 0?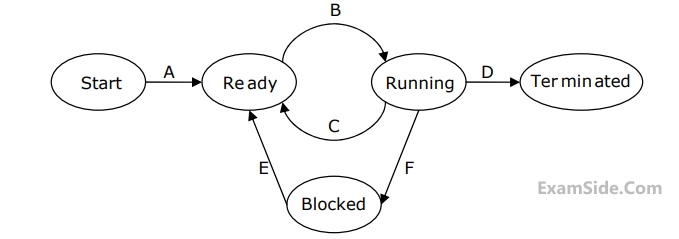
Now consider the following statements:
$$1.\,\,\,$$ If a process makes a transition $$D,$$ it would result in another process making transition $$A$$ immediately.
$$2.\,\,\,$$ $$A$$ process $${P_2}$$ in blocked state can make transition $$E$$ while another process $${P_1}$$ is in running state.
$$3.\,\,\,$$ The $$OS$$ uses preemptive scheduling.
$$4.\,\,\,$$ The $$OS$$ uses non-preemptive scheduling.
Which of the above statements are TRUE?
void enter_CS(X) {
while test-and-set(X) ;
}
void leave_CS(X) {
X=0;
}I. The above solution to CS problem is deadlock-free
II. The solution is starvation free.
III. The processes enter CS in FIFO order.
IV More than one process can enter CS at the same time.
Which of the above statements is TRUE?
$${\rm I}.\,\,\,\,\,\,\,\,\,\,\,$$ Content coupling
$${\rm II}.\,\,\,\,\,\,\,\,\,$$ Common coupling
$${\rm III}.\,\,\,\,\,\,\,$$ Control coupling
$${\rm IV}.\,\,\,\,\,\,\,$$ Stamp coupling
$${\rm V}.\,\,\,\,\,\,\,\,\,$$ Data coupling
Coupling between modules can be ranked in the order of strongest (least desirable) to weakest (most desirable) as follows.
$${\rm I}.\,\,\,\,\,\,$$ The cyclomatic complexity of a module is equal to the maximum number of
$$\,\,\,\,\,\,\,\,\,\,\,$$linearly independent circuits in the graph.
$${\rm II}.\,\,\,$$ The cyclomatic complexity of a module is the number of decisions in the
$$\,\,\,\,\,\,\,\,\,\,$$module plus one, where a decision is effectively any conditional statement in
$$\,\,\,\,\,\,\,\,\,\,$$the module.
$${\rm III}\,$$ The cyclomatic complexity can also be used as a number of linearly
$$\,\,\,\,\,\,\,\,\,\,$$independent paths that should be tested during path coverage testing.
$${\rm I}.\,\,\,\,\,\,$$ The content diagram should depict the system as a single bubble.
$${\rm II}.\,\,\,\,$$ External entities should be identified clearly at all levels of $$DFDs$$
$${\rm III}.\,\,$$ Control information should not be represented in $$DFD$$
$${\rm IV}.\,\,$$ A data store can be connected either to another data store or to an external
$$\,\,\,\,\,\,\,\,\,\,\,\,$$entity.
$${L_1} = \left\{ {{a^m}{b^m}\,c\,{a^n}{b^n}\left| {m,n \ge 0} \right.} \right\}$$
$${L_2} = \left\{ {{a^i}{b^i}{c^k}\left| {i,j,k \ge 0} \right.} \right\}$$ Then $$L$$ is

The above $$DFA$$ accepts the set of all strings over $$\left\{ {0,\,\,1} \right\}$$ that
The language generated by the above grammar over the alphabet $$\left\{ {a,\,b} \right\}$$ is the set of